Data Centre and Colocation Certifications
Mon, 25 Feb 2013
data centres, colocation
When researching colocation and data centre providers based in London, many customers encounter certification standards such as ISO 27001 and PCI DSS. These can be confusing, and sometimes misleading, without some idea of how they relate to the data centre industry.
ISO 27001
Developed by the International Organization for Standardization, ISO 27001 is fundamentally an information management standard: in order to acquire ISO 27001, an organisation must demonstrate that it has comprehensive operational controls over the acquisition, storage and destruction of data. Importantly, this standard contains many information security criteria, from software file access auditing to CCTV coverage and other physical security measures. It therefore is most applicable in the administrative back-office of any organisation.
Many data centre owners/operators have been certified against ISO 27001. However, as ISO 27001 fundamentally regards information management, rather than physical/software/network security, there is often some misunderstanding.
For some customers, it will be a staple requirement that their data centre is compliant in order that they can themselves become compliant with relevant parts of the certification (with an emphasis on physical security, access auditing, CCTV etc.). However, other customers may assume the ISO of their data centre absolves them from all responsibility for their equipment, network and operations - that the ISO can be "adopted" merely by being within the same building - which of course is false.
ISO 27001 is focussed on an individual organisation's responsibilities for handling data, not on bricks and mortar, and is non-transferrable
Further, the complexity of the standard allows for some misconceptions about what it really offers. The Statement of Applicability can reveal some surprising declarations, as can be see in this extract from a popular UK cloud computing provider statement which avoids auditing against section A.10.6.2 by stating they do not provide any network services:
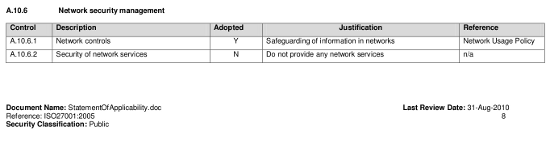
Therefore accreditation can be obtained without auditing one of the key (and complex) infrastructure components. Questions should be asked by customers of the relevance of ISO 27001 to a cloud provider who does not include their network in the auditing process.
ISO 27001 is by no means an easy standard to achieve; it is even less easy to maintain once auditors have left the building and stringent procedures need to be maintained with new staff trained and audited. Along with clarification of what has been audited, a simple request by customers to know when a provider was last audited may also be useful.
PCI DSS
The Payment Card Industry Data Security Standard is an American standard set on behalf of the major card payment companies such as Visa and MasterCard. With an e-commerce heavy Internet, it is perhaps one of the most common standards referred to during data centre and colocation due diligence. Its criteria also cover what most businesses will think about in terms of security of "sensitive data" - exemplified in PCI DSS by storing card holder details (although in practice, of course, it could be any similarly sensitive information).

PCI DSS comes in to force for two categories of businesses:
- Merchants: Online retailers who handle credit/debit cards must comply with the required PCI standards (see also a debate on the legal implications of PCI DSS for merchants)
- Payment service providers: These organisations, such as WorldPay and ePay, will handle card payments on behalf of many thousands of individual merchants. They are also known as payment gateway providers.
Whilst payment service providers require their own unique set of rules and standards, merchants are governed by the four PCI tiers:

The PCI DSS criteria require various Self Assessment Questionnaires (SAQs) to be completed depending on whether the merchant handles physical (terminal) cards or electronic transactions, if they store card details themselves or outsource this information, and if any data is transmitted over the Internet or other potentially insecure medium. Of the five SAQs available, the only one which is really applicable to colocation data centres is SAQ D, in particular section 9 Restrict physical access to cardholder data. Briefly, this mandates:
- Entry controls including access cards and/or key locks.
- CCTV on all sensitive areas, stored for at least 3 months
- Strict security procedures for temporary visitor access
- Physical security and inventory of all removable media
- Destruction of obsolete media (secure wipe, shred, incinerate)
The other 11 sections of PCI DSS refer to network and software security, and are not items that a colocation data centre or an Internet access provider are able to provide for. The onus on network security starts at the customer server or firewall, not on their network provider's systems. Whilst reputable data centres will ensure they can meet the above criteria (and may market as being "PCI DSS compliant"), it is ultimately the responsibility of the merchant - and not the data centre owner or Internet access operator - to ensure their systems are PCI compliant.
It is ultimately the responsibility of the merchant - and not the data centre - to ensure their systems are PCI compliant.
As with ISO 27001, customers should cut through the marketing and take care to investigate what they are really being offered in terms of compliance, and take time to understand how much responsibility really still lies within their own organisation.
Come join us on: